The cybersecurity community has recently been jolted by the latest 2024 Rapid7 “Attack Intelligence Report.” This comprehensive document has served as a stark eye-opener, revealing that an alarming 53% of the newly discovered vulnerabilities in late 2023 and early 2024 were zero-day exploits. These vulnerabilities, by definition, provide no prior warning, allowing attackers to strike multiple systems swiftly and devastatingly. The traditional strategy of simply patching vulnerabilities and hoping for divine intervention is insufficient. Patches can take days, sometimes weeks, to be developed and distributed, leaving systems exposed and vulnerable for far too long.
An imminent disaster caused by firmware evolution
According to the IoT Security Foundation’s (IoTSF) report titled “Software Bills of Materials for IoT and OT Devices,” the current state of firmware development for IoT devices is highly precarious. Modern IoT firmware is often a patchwork of various components, each potentially harboring its own vulnerabilities. This fragmented assembly process results in numerous security loopholes, making it exceedingly difficult for security teams to maintain a robust defense. Regularly fixing these issues is akin to playing a never-ending game of whack-a-mole, where new vulnerabilities surface as quickly as old ones are patched.
Catastrophic Dangers of Zero-Days
Zero-day vulnerabilities are a particularly prized weapon for state actors and malicious attackers. The infamous 2007 Idaho National Laboratory experiment demonstrated that the repercussions of such vulnerabilities extend far beyond data breaches and ransomware attacks. They can result in tangible, physical destruction. An attack leveraging zero-day vulnerabilities at scale could potentially cause catastrophic damage to critical infrastructure, leading to widespread disruption and potentially even loss of life.
MCUs’ Isolation Partitioning: A New Approach
The era of relying on the ‘patch and pray’ method must come to an end. Instead, we need to embrace isolated partitioning on Microcontroller Units (MCUs). By isolating critical firmware components and sandboxing potential threats, we can build a more resilient defense mechanism. Our analysis indicates that isolated partitioning can be effectively implemented on Cortex-M-based MCUs, which make up nearly 80% of all MCUs currently in production. This approach ensures that even if one partition is compromised, the damage is contained, preventing a full system breach.
Sandboxing Attackers: A Practical Approach
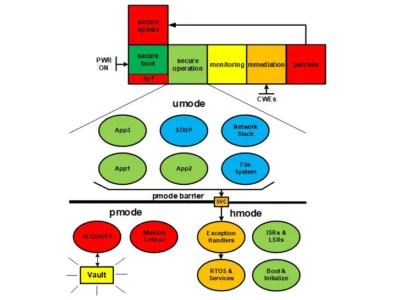
Our proposed design employs a mode barrier to protect mission-critical and security firmware while isolating more vulnerable application firmware in separate partitions. This strategy means that if an attacker manages to compromise a single partition, they are effectively trapped within a sandbox, unable to disrupt the entire system. This approach not only enhances security but also reduces insider threats and promotes best programming practices. By containing potential breaches, we can limit the scope of any attack and safeguard the integrity of the overall system.
Conclusion
n conclusion, isolated partitioning offers a robust solution to the pervasive issue of zero-day vulnerabilities and unpatched exploits. By prioritizing isolation and granular security measures, we can build a more secure digital future. The time for action is now. It is imperative that we protect our IoT devices against the ever-evolving landscape of cyber threats. The implementation of isolated partitioning on MCUs represents a significant step forward in fortifying our defenses and ensuring the safety and reliability of our interconnected world.


